
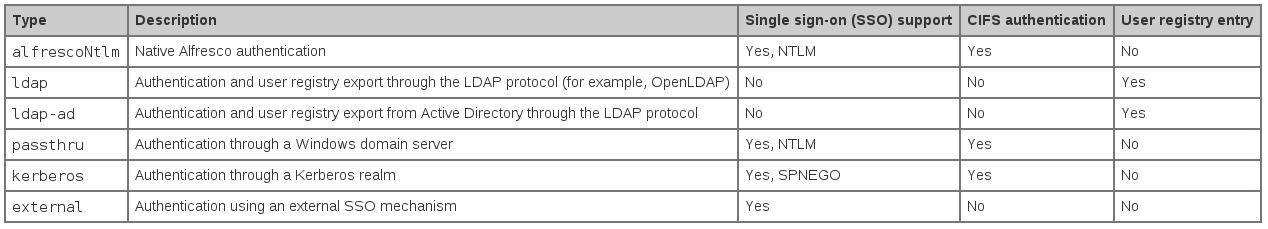
The Alfresco Authentication Chain supports multiple alternative implementations of authentication subsystem, each designed to work with one of the different types of back-end authentication systems like AD, LDAP, Kerberos, alfrescoNtlm (default in the built-in auth) or other external servers. The Alfresco official wiki shows the following table with the list of the authentication subsystem types supplied with Alfresco.
In this post I show how to integrate Alfresco with the two LDAP subsystems, OpenLDAP and Active Directory. More info about the Alfresco Authentication Susbsystems can be found here.
EXAMPLE 1. – Subsystem ldap, integration with Netscape Directory Server (NDS)
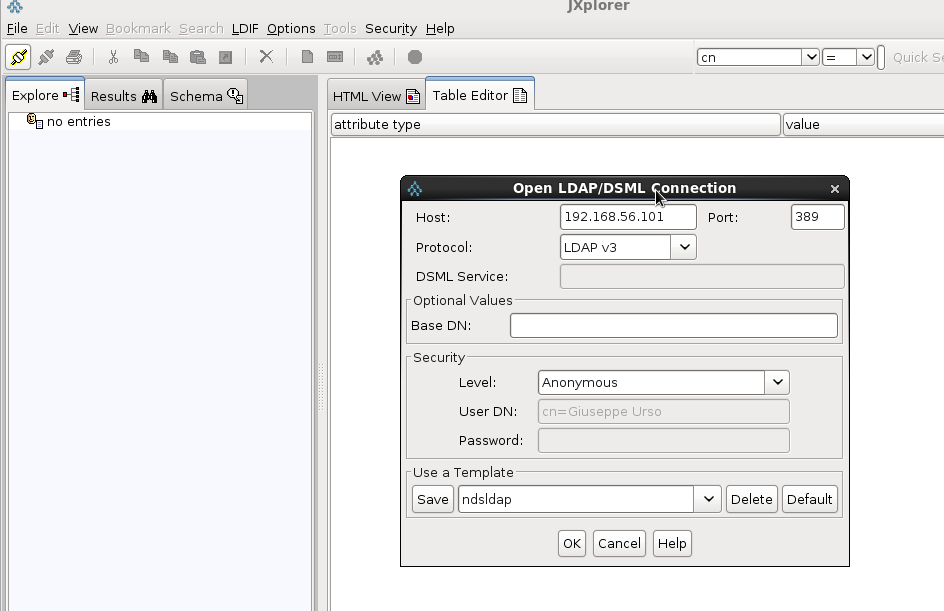
In this example I use a rebuild of Netscape Directory Server (NDS) called CentOS Directory Server, a LDAP solution for CentOS Linux server distributions. Other LDAP systems coming from NDS are: Red Hat Directory Server, Fedora 389 Directory Server, Sun One Directory Server. To test and better manipulate ldap users, I use JXplorer, a open source ldap client written in java. Here the application stack.
Alfresco: Community 4.0.e
LDAP Server: CentOS Directory Server 8.2
LDAP Client: JXplorer 3.3
The first operation to do is a test of ldap connection using the anonymous access against the ldap server CentOS-DS (LDAPv3).
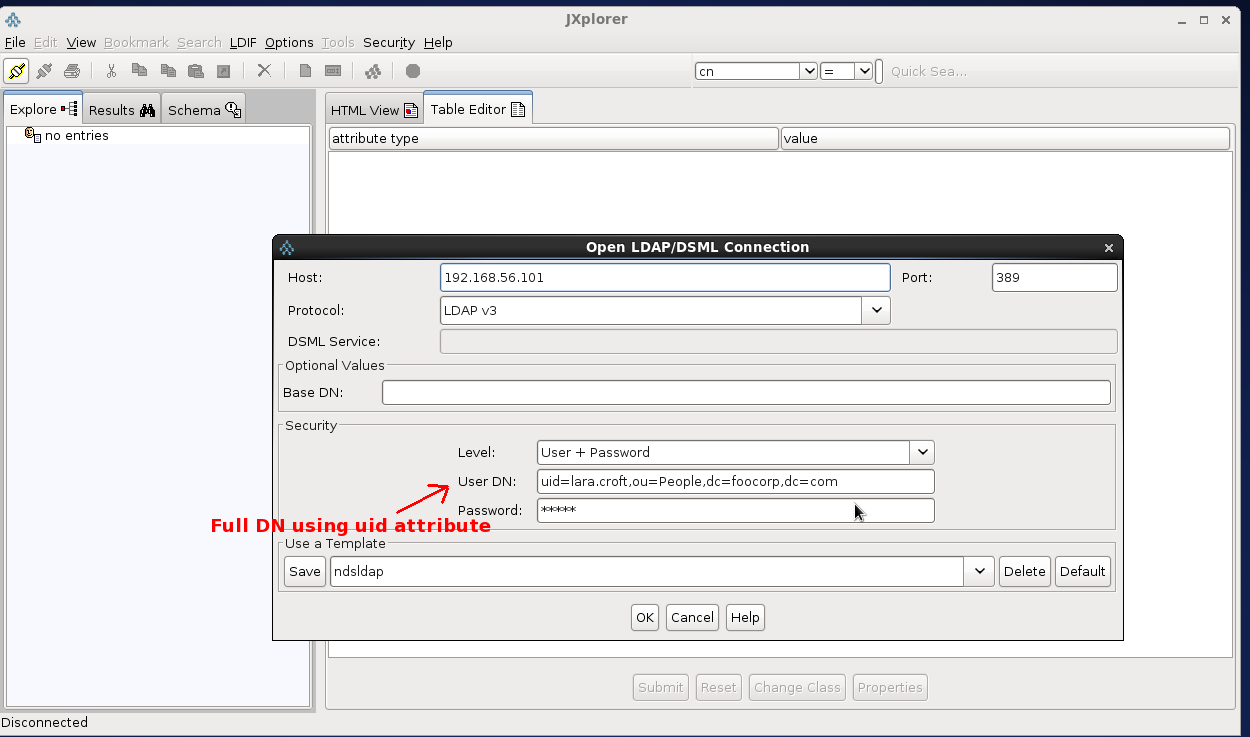
Furthermore we can test ldap authentication using the credentials of a user. Use the full Distinguished Name (DN) in the BIND request, here two examples:
DN: cn=Lara Croft,ou=People,dc=foocorp,dc=com DN: uid=lara.croft,ou=People,dc=foocorp,dc=com
Pay attention to the attributes cn and uid in the DN. The exact DN expression is very important in order to correctly set ldap.authentication.userNameFormat, the Alfresco property that specifies how to map the user identifier entered by the user in the login.
Here the ldif format for LDAP Users and Groups in this example.
– LDAP USER
DN: uid=lara.croft,ou=People,dc=foocorp,dc=com objectClass: person objectClass: top objectClass: inetOrgPerson objectClass: organizationalPerson cn: Lara Croft givenName: Lara sn: Croft uid: lara.croft
– LDAP GROUP
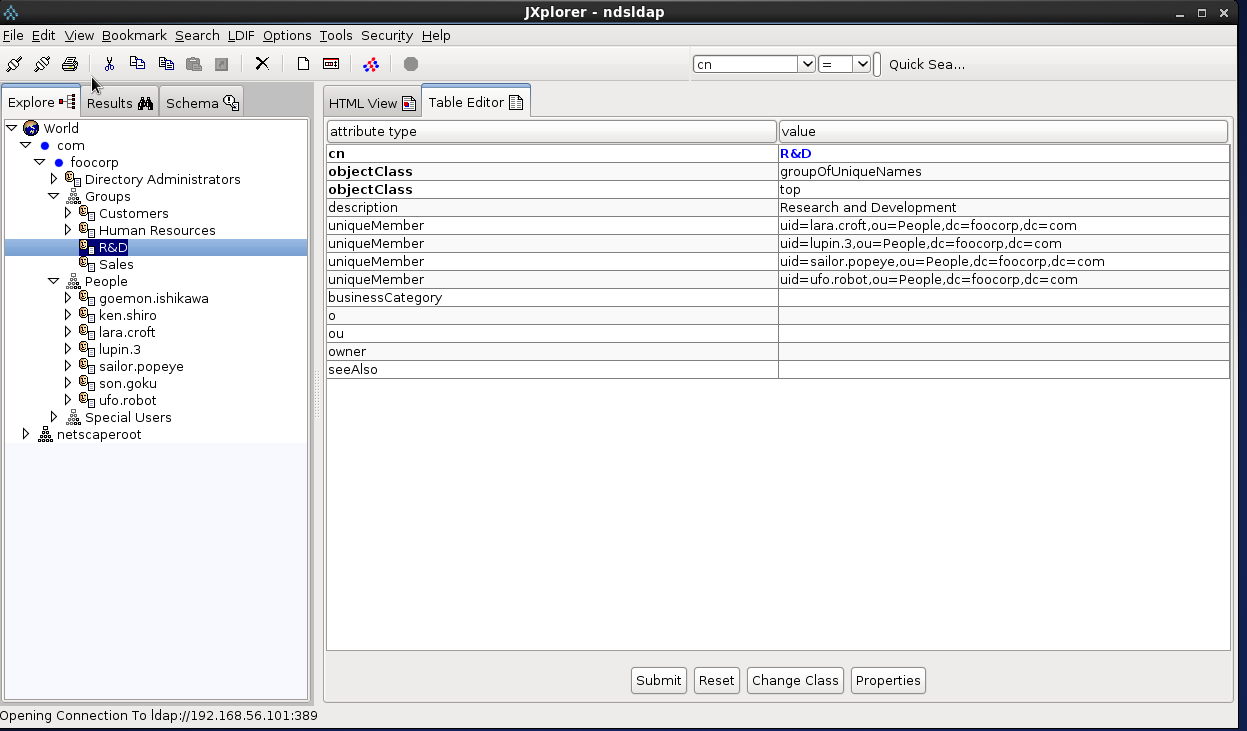
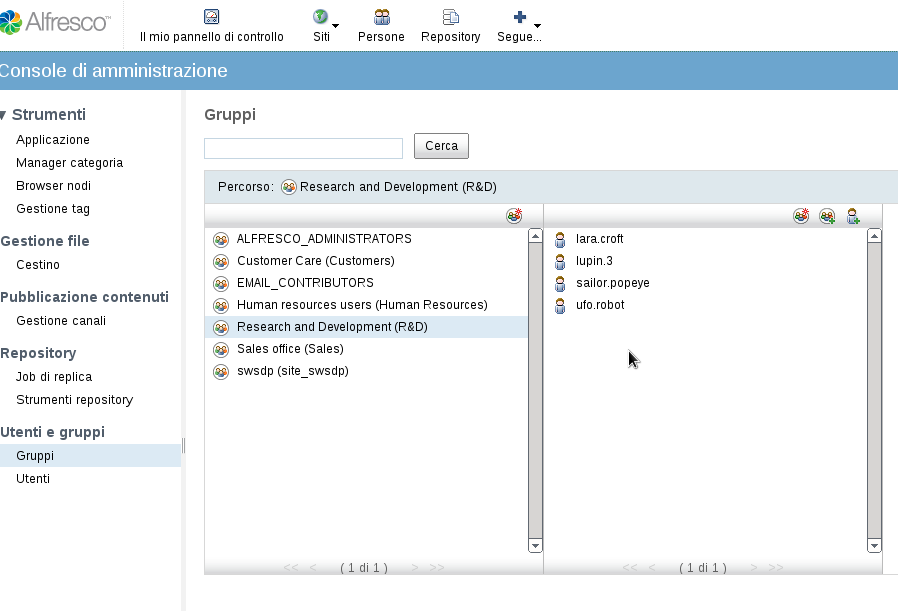
DN: cn=R&D,ou=Groups,dc=foocorp,dc=com objectClass: groupOfUniqueNames objectClass: top cn: R&D description: Research and Development uniqueMember: uid=lara.croft,ou=People,dc=foocorp,dc=com uniqueMember: uid=sailor.popeye,ou=People,dc=foocorp,dc=com uniqueMember: uid=ufo.robot,ou=People,dc=foocorp,dc=com uniqueMember: uid=lupin.3,ou=People,dc=foocorp,dc=com
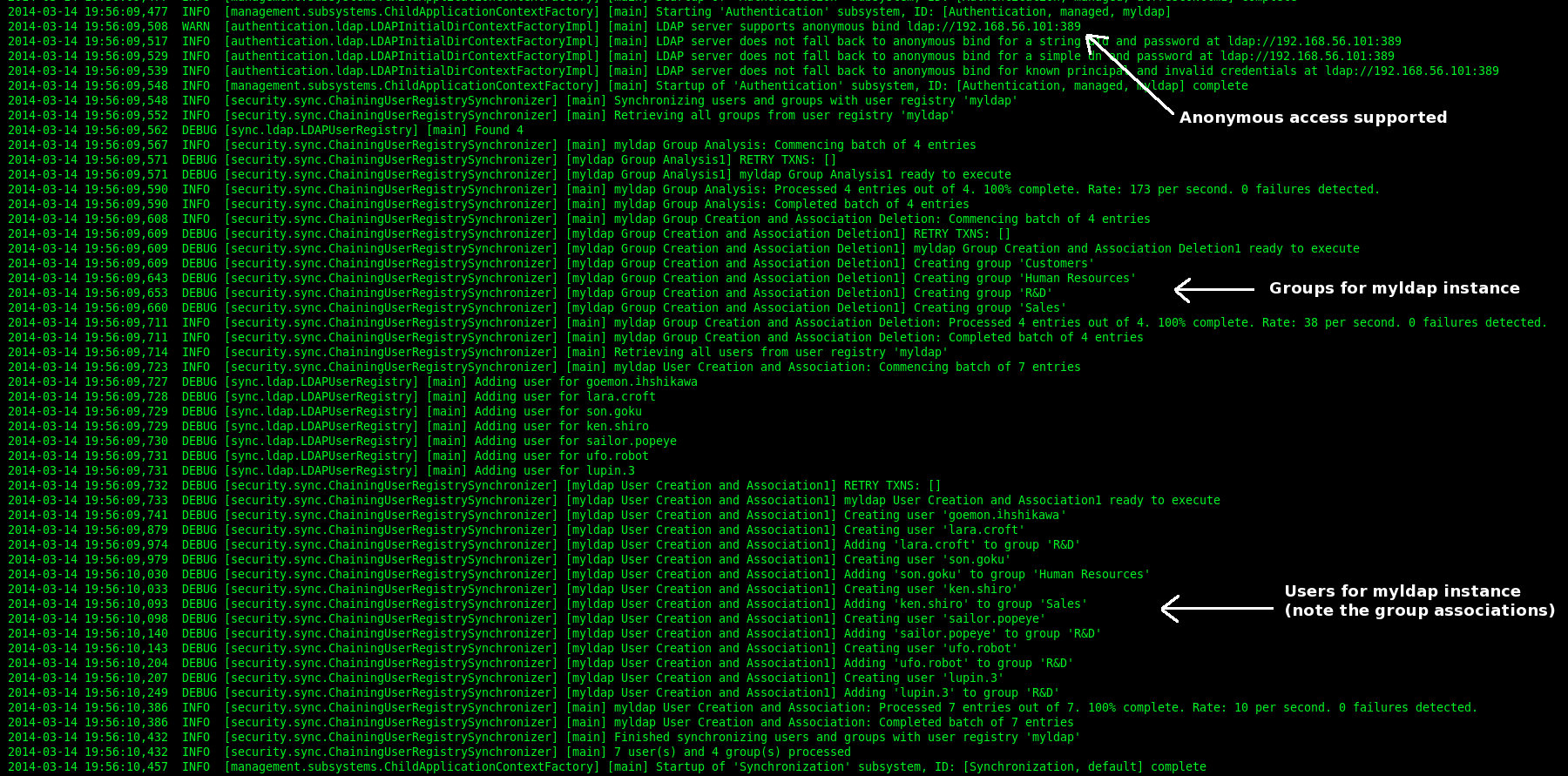
In this example I also configure the LDAP syncronization mechanism based on the Alfresco “user registry export” service. Here the four steps to integrate Alfresco with Centos-DS LDAP server (authentication and syncronization).
1. Create the properties files to configure myldap instance
$ mkdir {ALFRESCO_HOME}/shared/classes/alfresco/extension/subsystems/Authentication/myldap
$ cd {ALFRESCO_HOME}/tomcat/webapps/alfresco/WEB-INF/classes/alfresco/subsystems/Authentication/
$ cp ./ldap/*.properties {ALFRESCO_HOME}/shared/classes/alfresco/extension/subsystems/Authentication/ldap/myldap
2. Edit the file ldap-authentication.properties to define myldap set up
ldap.authentication.active=true
# Full DN format to login
ldap.authentication.userNameFormat=uid=%s,ou=People,dc=foocorp,dc=com
ldap.authentication.java.naming.provider.url=ldap://192.168.56.101:389
ldap.synchronization.active=true
# Anonymous access for sync
ldap.synchronization.java.naming.security.authentication=none
ldap.synchronization.groupQuery=(objectclass\=groupOfUniqueNames)
ldap.synchronization.groupDifferentialQuery=(&(objectclass\=groupOfUniqueNames)(!(modifyTimestamp<\={0})))
ldap.synchronization.personQuery=(objectclass\=inetOrgPerson)
ldap.synchronization.personDifferentialQuery=(&(objectclass\=inetOrgPerson)(!(modifyTimestamp<\={0})))
ldap.synchronization.groupSearchBase=ou\=Groups,dc\=foocorp,dc\=com
ldap.synchronization.userSearchBase=ou\=People,dc\=foocorp,dc\=com
ldap.synchronization.userIdAttributeName=uid
ldap.synchronization.userFirstNameAttributeName=givenName
ldap.synchronization.userLastNameAttributeName=sn
ldap.synchronization.userEmailAttributeName=mail
ldap.synchronization.userOrganizationalIdAttributeName=o
ldap.synchronization.defaultHomeFolderProvider=largeHomeFolderProvider
ldap.synchronization.groupIdAttributeName=cn
ldap.synchronization.groupDisplayNameAttributeName=description
ldap.synchronization.groupType=groupOfUniqueNames
ldap.synchronization.personType=inetOrgPerson
ldap.synchronization.groupMemberAttributeName=uniqueMember
3. Add the following properties to the alfresco-global.properties file
# LDAP authentication.chain=alfrescoNtlm1:alfrescoNtlm,myldap:ldap synchronization.sinchronyzeChangesOnly=false synchronization.syncWhenMissingPeopleLogIn=true synchronization.syncOnStartup=true synchronization.import.cron=0 0 18 * * ?
4. Optionally enable debugging in the log4j.properties file
#LDAP log4j.logger.org.alfresco.repo.importer.ImporterJob=debug log4j.logger.org.alfresco.repo.importer.ExportSourceImporter=debug log4j.logger.org.alfresco.repo.security.authentication.ldap=debug log4j.logger.org.alfresco.repo.security.sync=debug #log4j.logger.org.alfresco.repo.security.sync=info
Follows the user name format I set in Alfresco:
ldap.authentication.userNameFormat=uid=%s,ou=People,dc=foocorp,dc=com
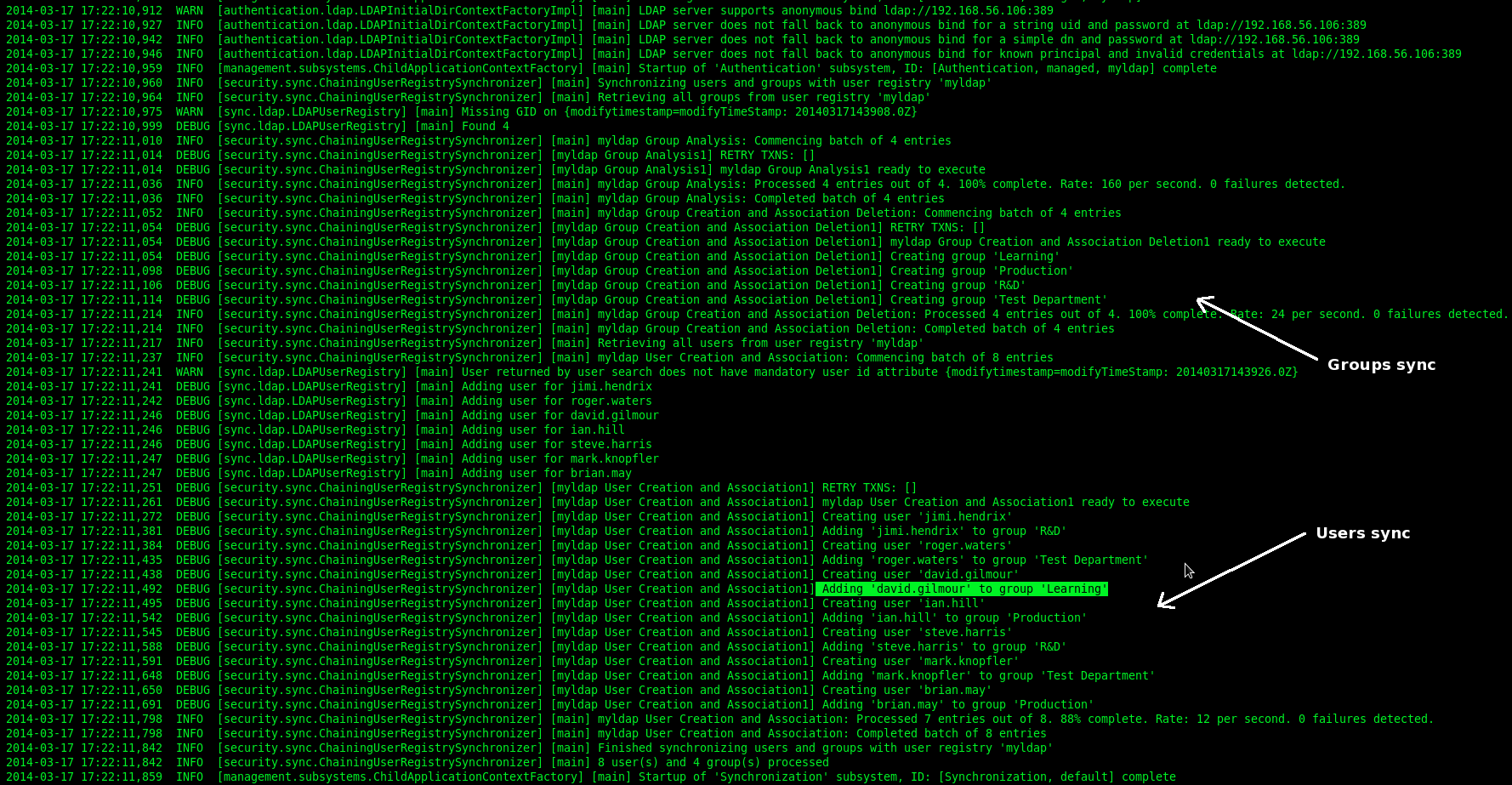
If no errors occurs you will get the following log messages on Alfresco bootstrap (synchronization.syncOnStartup=true).
EXAMPLE 2. – Subsystem ldap-ad, integration with Microsoft Active Directory
In this example I integrate Alfresco and Microsoft Acrive Directroy. I use a test environment where a instance of Microsoft Active Directory Server 2003 is running. Here the application stack.
Alfresco: Community 4.0.e
LDAP Server: Microsoft Active Directory 2003
LDAP Client: JXplorer 3.3
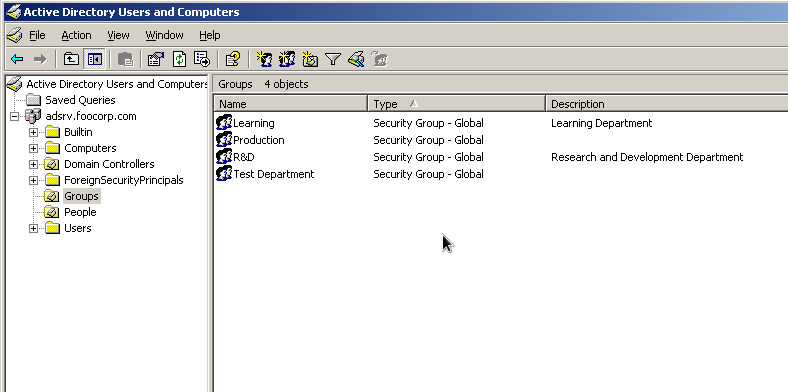
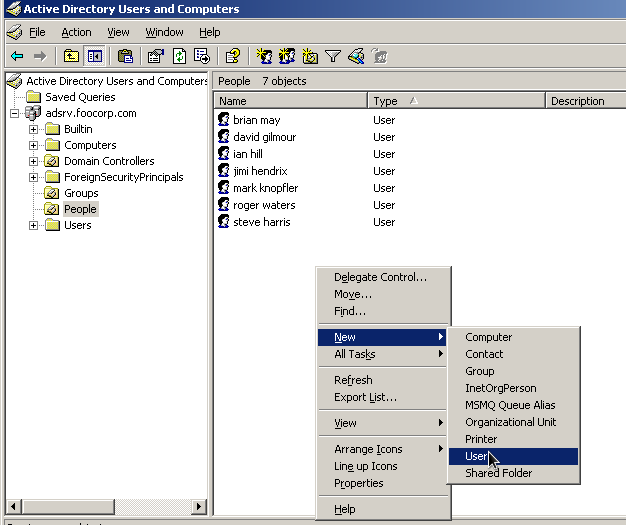
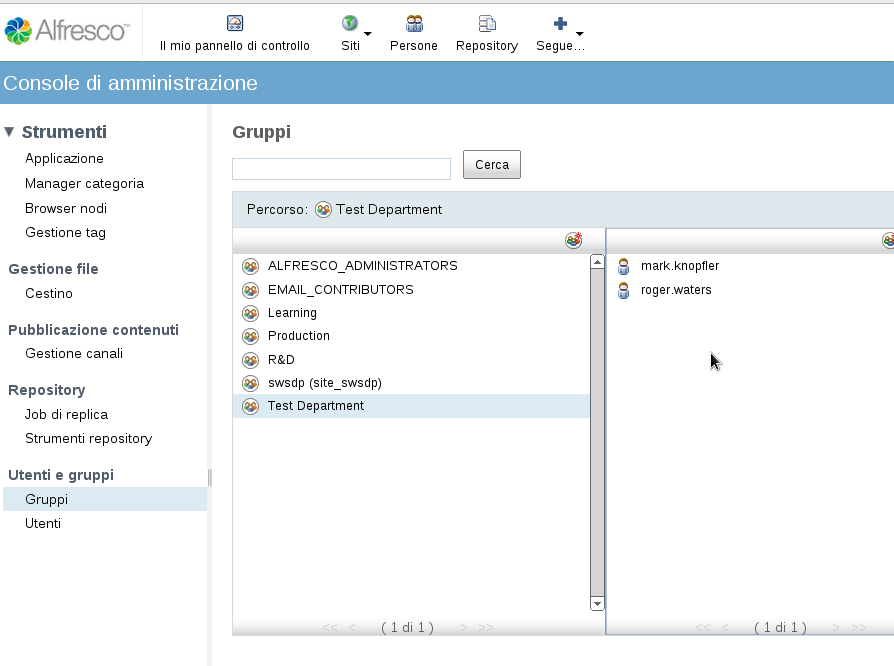
I create the two Organiztional Units Groups and People for groups and users.
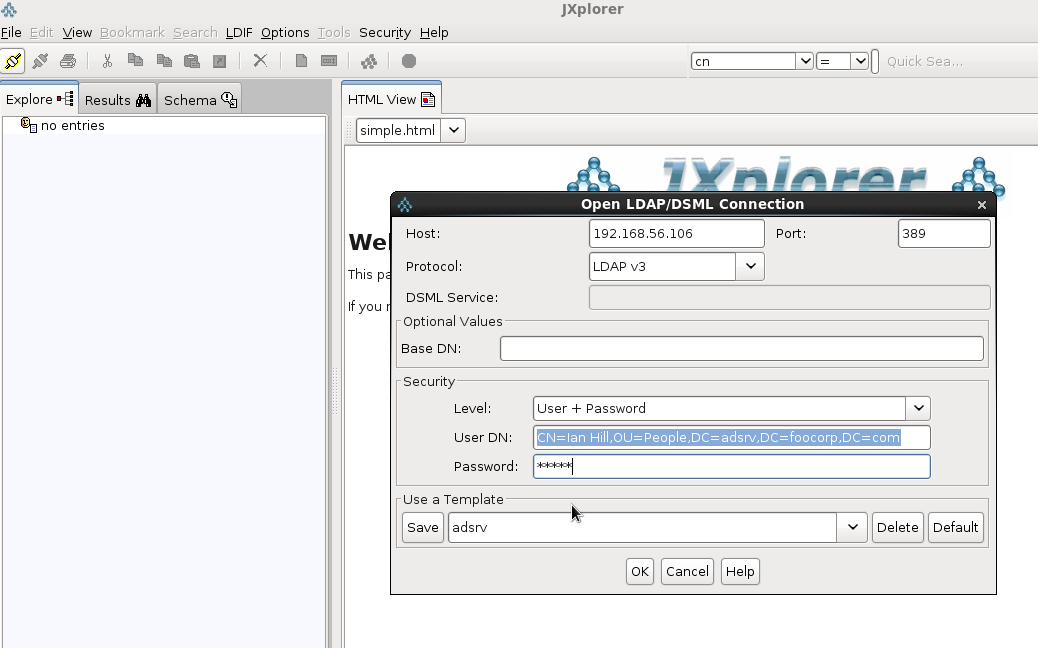
Use JXplorer to test the ldap connection and authentication. Insert the full Distinguished Name (DN) in the BIND request. In this case I use the cn attribute in the full DN:
DN: CN=ian hill,OU=People,DC=adsrv,DC=foocorp,DC=com
Follows the ldif format for LDAP Users and Groups in this example.
– LDAP-AD Group
DN: CN=R&D,OU=Groups,DC=adsrv,DC=foocorp,DC=com objectClass: top objectClass: group cn: R&D description: Research and Development Department distinguishedName: CN=R&D,OU=Groups,DC=adsrv,DC=foocorp,DC=com groupType: -2147483646 instanceType: 4 member: CN=steve harris,OU=People,DC=adsrv,DC=foocorp,DC=com member: CN=jimi hendrix,OU=People,DC=adsrv,DC=foocorp,DC=com name: R&D objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=adsrv,DC=foocorp,DC=com objectGUID:: RmNuVu+/ve+/vSxJ77+9RUt0Xkfvv70Y objectSid:: AQUAAAAAAAUVAAAA77+977+9be+/ve+/vTnvv71xS++/ve+/vQZUBAAA sAMAccountName: R&D sAMAccountType: 268435456
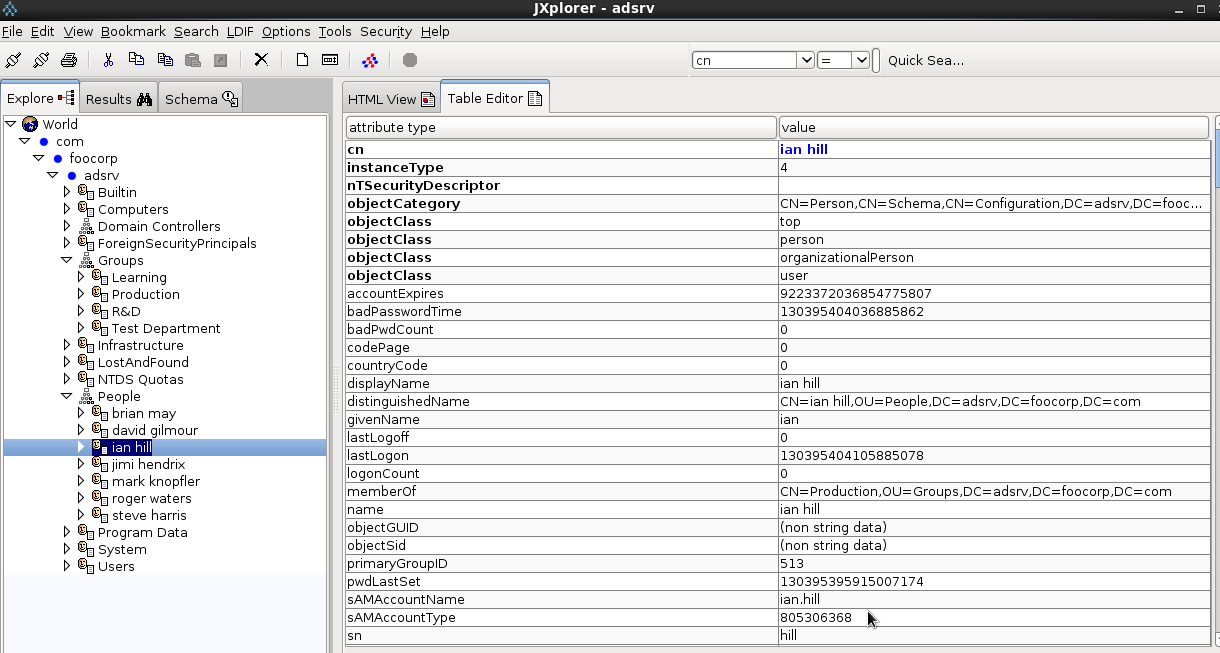
– LDAP-AD User
DN: CN=brian may,OU=People,DC=adsrv,DC=foocorp,DC=com objectClass: top objectClass: person objectClass: organizationalPerson objectClass: user accountExpires: 9223372036854775807 cn: brian may displayName: brian may distinguishedName: CN=brian may,OU=People,DC=adsrv,DC=foocorp,DC=com givenName: brian memberOf: CN=Production,OU=Groups,DC=adsrv,DC=foocorp,DC=com name: brian may objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=adsrv,DC=foocorp,DC=com sAMAccountName: brian.may sAMAccountType: 805306368 sn: may userAccountControl: 512 userPrincipalName: brian.may@adsrv.foocorp.com
For the user name format in Alfresco I use the following expression:
sAMAccountName@adsrv.foocorp.com
Here the four steps to integrate Alfresco with Microsoft Active Directory server (authentication and syncronization).
1. Create the properties files to configure myldap instance
$ mkdir {ALFRESCO_HOME}/shared/classes/alfresco/extension/subsystems/Authentication/ldap-ad/myldap
$ cd {ALFRESCO_HOME}/tomcat/webapps/alfresco/WEB-INF/classes/alfresco/subsystems/Authentication/
$ cp ./ldap-ad/*.properties {ALFRESCO_HOME}/shared/classes/alfresco/extension/subsystems/Authentication/ldap-ad/myldap
2. Edit the file ldap-authentication.properties to define myldap set up
ldap.authentication.active=true ldap.authentication.userNameFormat=%s@adsrv.foocorp.it ldap.authentication.java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory ldap.authentication.java.naming.provider.url=ldap://192.168.56.106:389 ldap.synchronization.active=true ldap.synchronization.java.naming.security.authentication=simple ldap.synchronization.java.naming.security.principal=ian.hill@adsrv.foocorp.it ldap.synchronization.java.naming.security.credentials=12345 ldap.synchronization.groupQuery=(objectclass\=*) ldap.synchronization.groupDifferentialQuery=(objectclass\=*) ldap.synchronization.personQuery=(objectclass\=*) ldap.synchronization.personDifferentialQuery=(objectclass\=*) ldap.synchronization.groupSearchBase=ou\=Groups,dc\=adsrv,dc\=foocorp,dc\=com ldap.synchronization.userSearchBase=ou\=People,dc\=adsrv,dc\=foocorp,dc\=com ldap.synchronization.modifyTimestampAttributeName=modifyTimestamp ldap.synchronization.timestampFormat=yyyyMMddHHmmss'.0Z' ldap.synchronization.userIdAttributeName=sAMAccountName ldap.synchronization.userFirstNameAttributeName=givenName ldap.synchronization.userLastNameAttributeName=sn ldap.synchronization.userEmailAttributeName=mail ldap.synchronization.userOrganizationalIdAttributeName=company ldap.synchronization.defaultHomeFolderProvider=largeHomeFolderProvider ldap.synchronization.groupIdAttributeName=cn ldap.synchronization.groupDisplayNameAttributeName=displayName ldap.synchronization.groupType=group ldap.synchronization.personType=user ldap.synchronization.groupMemberAttributeName=member ldap.synchronization.enableProgressEstimation=true
3. Add the following properties to the alfresco-global.properties file
# LDAP authentication.chain=alfrescoNtlm1:alfrescoNtlm,myldap:ldap-ad synchronization.sinchronyzeChangesOnly=true synchronization.syncWhenMissingPeopleLogIn=true synchronization.syncOnStartup=true synchronization.import.cron=0 0 18 * * ?
4. Optionally enable debugging in the log4j.properties file
#LDAP log4j.logger.org.alfresco.repo.importer.ImporterJob=debug log4j.logger.org.alfresco.repo.importer.ExportSourceImporter=debug log4j.logger.org.alfresco.repo.security.authentication.ldap=debug log4j.logger.org.alfresco.repo.security.sync=debug #log4j.logger.org.alfresco.repo.security.sync=info
 English
English Italian
Italian







Thanks a lot for your great documentation !
Bookmarked !
Very interesting Giù ;)
Thanks guy!!! ;-)
Thank you for your deep understanding document. It worked for me.
Past two weeks i am working on alfresco 4.2 integration with liferay 6.2 for document management. I imported AD users success in both tools and they are all able to login individually. I would like to set up SSO and auto login in browsers. Please guide me to set up auto login and SSO for alfresco.
All your words valuable for me.Thank you
Hi Gerorge,
I’m happy to hear this post was useful!
The scenario you’ve described is very common in a enterprise environment. The Alfresco-Liferay integration is a widely used practice. Unfortunately in this context I don’t have a lot to say about the web SSO…As you’ve already figured out, this is my job and an Alfresco specialist is paid to do consulting, you know.
However I can suggest you to take a look at CAS, a widely used single sign-on solution for the web. It works well both with Alfresco and Liferay.
Here is some links that could be useful:
https://wiki.jasig.org/display/CAS/Home
http://www.liferay.com/it/community/wiki/-/wiki/Main/CAS+Liferay+6+Integration
https://wiki.alfresco.com/wiki/Central_Authentication_Service_Configuration
Giuseppe
Thank you Giuseppe Urso for your quick reply. Here is my situation how do i work. My active directory server is available in intranet. i connected through Cisco Secure mobility client (VPN). When i try to access http://xx.xx.xx.xx:8080/alfresco the browser gives pop up. It requires for intranet user credential to login. With out this login pop up user must be able to login(Login must done in back end).
Sorry to trouble Urso, i am a student and i do some part time jobs. i am unable to pay you by now. please help me.
Thank you for your golden time.
George,
when you ask for the url http://host:8080/alfresco , what is the exact browser response?
Does it show the default Alfresco login page ?
Reading your description, It seems that all http requests are filtered by a proxy web server. The login popup could come from a web proxy. Alfresco has not a popup login, but simply a web page form like the image I’ve posted in the article.
If this is all wrong, then maybe you want a direct access into Alfresco without a login page. In this case, as I already said, you must configure a web SSO like CAS.
Remember that Alfresco like Liferay contain private areas so you must be logged in to see their pages. Use CAS as central front-end login system. It will manages the authentication chain to your back-end applications like Alfresco, Liferay and so on.
PS: You have posted the same reply two time. Please the next time, post a single comment.
Giuseppe
I am using cas-server-4.0.0-release and apache-tomcat-7.0.55 When i run tomcat i get this
Error:You are currently accessing CAS over a non-secure connection. Single Sign On WILL NOT WORK. In order to have single sign on work, you MUST log in over HTTPS
i googled but i could not fixed it
i followed this demo document till step:4 https://wiki.jasig.org/display/CASUM/Demo
in server.xml file i added
and un commented
i did nothing more than that also i tried with old version of CAS but tomcat remains the same
Hi,
I have a similar requirement like the one Mr.George explained. Are you available to do this task for me? We can negotiate on the amount. Please give me your skype details or email details. I will touch you directly.
Hi Vivek,
at the moment I’m very busy with my job, but I will see if I can give you some help.
Check your email, I sent you some info.
Giuseppe
Hi friends,
I am using cas-server-4.0.0-release and apache-tomcat-7.0.55 When i run tomcat i get this Error:You are currently accessing CAS over a non-secure connection. Single Sign On WILL NOT WORK. In order to have single sign on work, you MUST log in over HTTPS. I googled but i could not fixed it. I followed this demo document till step:4 https://wiki.jasig.org/display/CASUM/Demo in server.xml file. I added and un commented i did nothing more than that also i tried with old version of CAS but tomcat remains the same
Hi,
as the error message says you must configure CAS to work with HTTPS (pay attention, no HTTP). The CAS official wiki writes:
“By default, CAS only sends the single sign on cookie (CASTGC) over secure connections; in other words it is not sent over a plain HTTP channel”.
In order to successfully enable the Tomcat HTTPS connector, you need a keystore. For example you can use “keytool” to create a self-signed certificate. When you uncomment the SSL entries in the server.xml file, you must have a keystore and a truststore to ensure the HTTPS channel.
Take a look here:
http://www.maximporges.com/2009/11/18/configuring-tomcat-ssl-clientserver-authentication/
Giuseppe
Thanks for sharing your knowledge…